
Happy World Password Day!
I know. There’s a day for every little thing and—really, World Password Day? It may seem silly but, first celebrated in 2013, the day does serve as a reminder of the importance of good password hygiene. Of course, like Mother’s Day and Father’s Day, we all know that, really, EVERY day is World Password Day. Because you can’t afford to have weak passwords.
Since securing access is our bread and butter (about which we are geekily passionate), we took the opportunity to do a survey of 600 IT professionals, 300 in the US and 300 in the UK, to understand how they’re protecting passwords and how well they believe their companies are doing. You can view the full Password Practices 2019 study results. If you just want the quickest summary, see our infographic about the US password practices results and the UK results. Or, read on for a summary of the highlights from our 2019 survey.
The Good News about Passwords
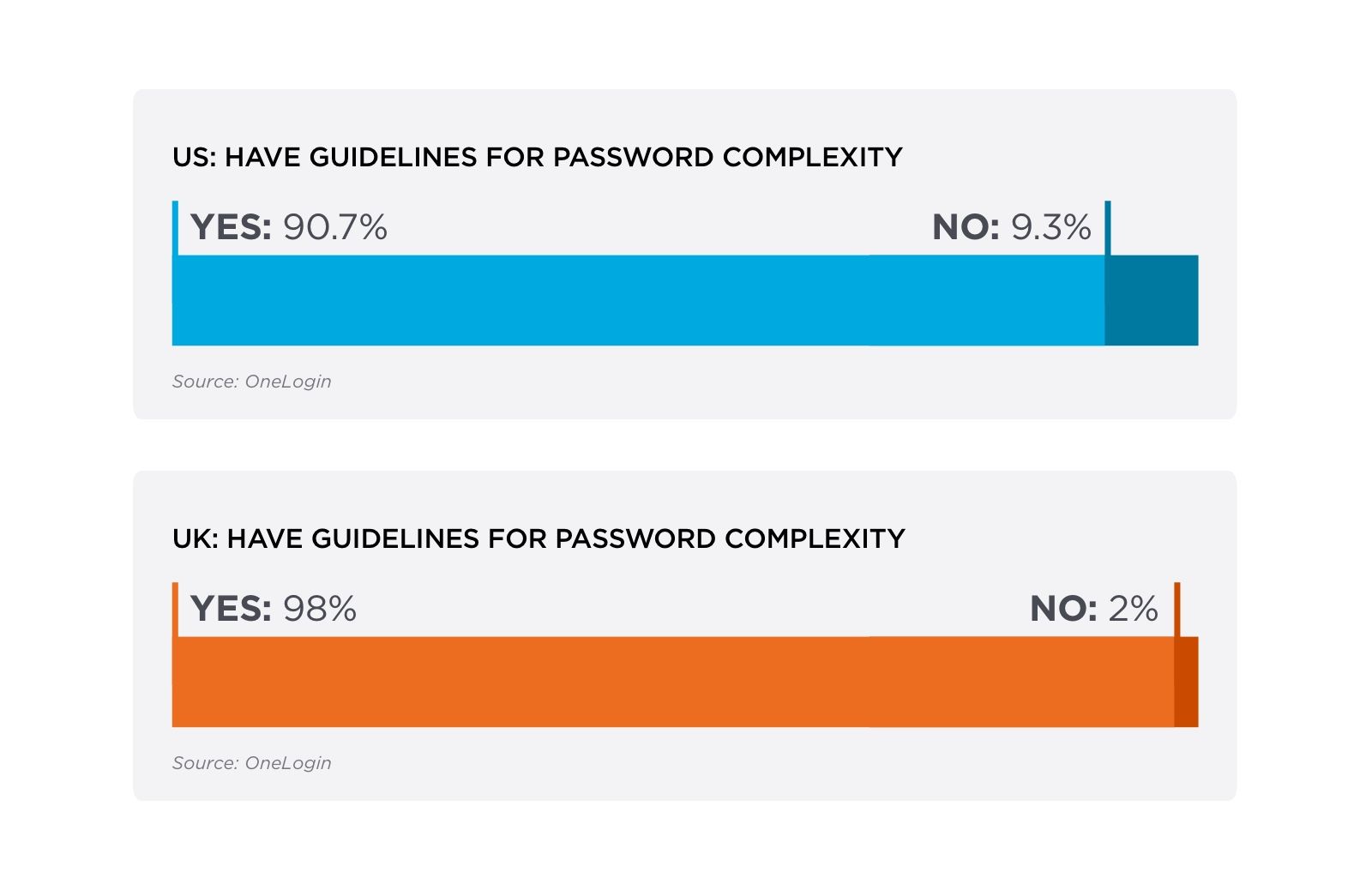
The good news is that by and large companies in the US and UK have implemented guidelines and best practices for passwords. And they generally comply with the older NIST guidelines for complex passwords including using:
- Minimum lengths for passwords
- A mix of uppercase and lowercase characters
- Numbers
- Special characters
Our survey also found that the vast majority of IT professionals believe their password protection methods are adequate, 92% in the US and 95% in the UK.
But let’s face it, that’s only good news if it’s true. Which brings us to the bad.
The Bad News about Passwords
While companies have implemented password guidelines, they aren’t meeting the newest NIST requirements nor implementing some of the most important ones.
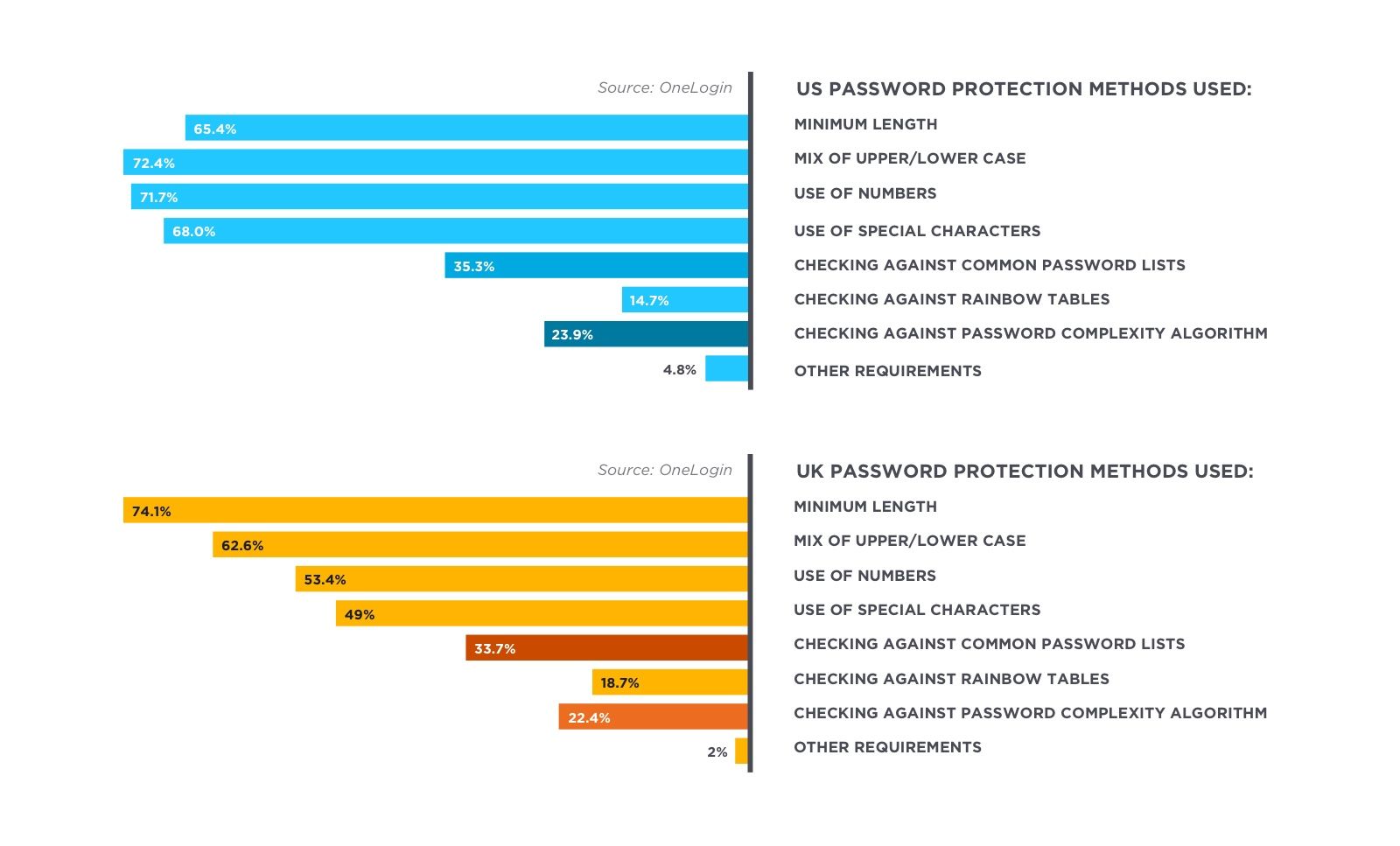
Companies have implemented complex passwords. But they mostly haven’t implemented key tools like checking passwords against common password lists and rainbow tables or using complexity algorithms.
NIST recently changed their guidelines, calling for easy to remember but hard to guess passwords. They eliminated the requirement for special characters (though they still allow them) and they recommended not requiring too-frequent password rotation.
That’s because when you require complex passwords and then change them frequently, users can’t remember their passwords. This results in users either re-using the same complex password everywhere or writing down or otherwise noting their passwords in insecure locations (Post-It notes, messages to themselves, spreadsheets). Either of these reduces password security and negates the whole point of complex passwords.
Nevertheless, we found many companies still requiring frequent password rotations.
A full third of US companies and over 40% of UK companies required resets monthly or more frequently. That frequency is an even bigger problem when you consider the ugly figures for the number of apps that require separate credentials.
The Truly Ugly News about Passwords
One of the most troubling statistics to come out of our survey is just how many passwords employees are expected to remember. We asked US and UK IT professionals how many apps they have that require separate credentials.
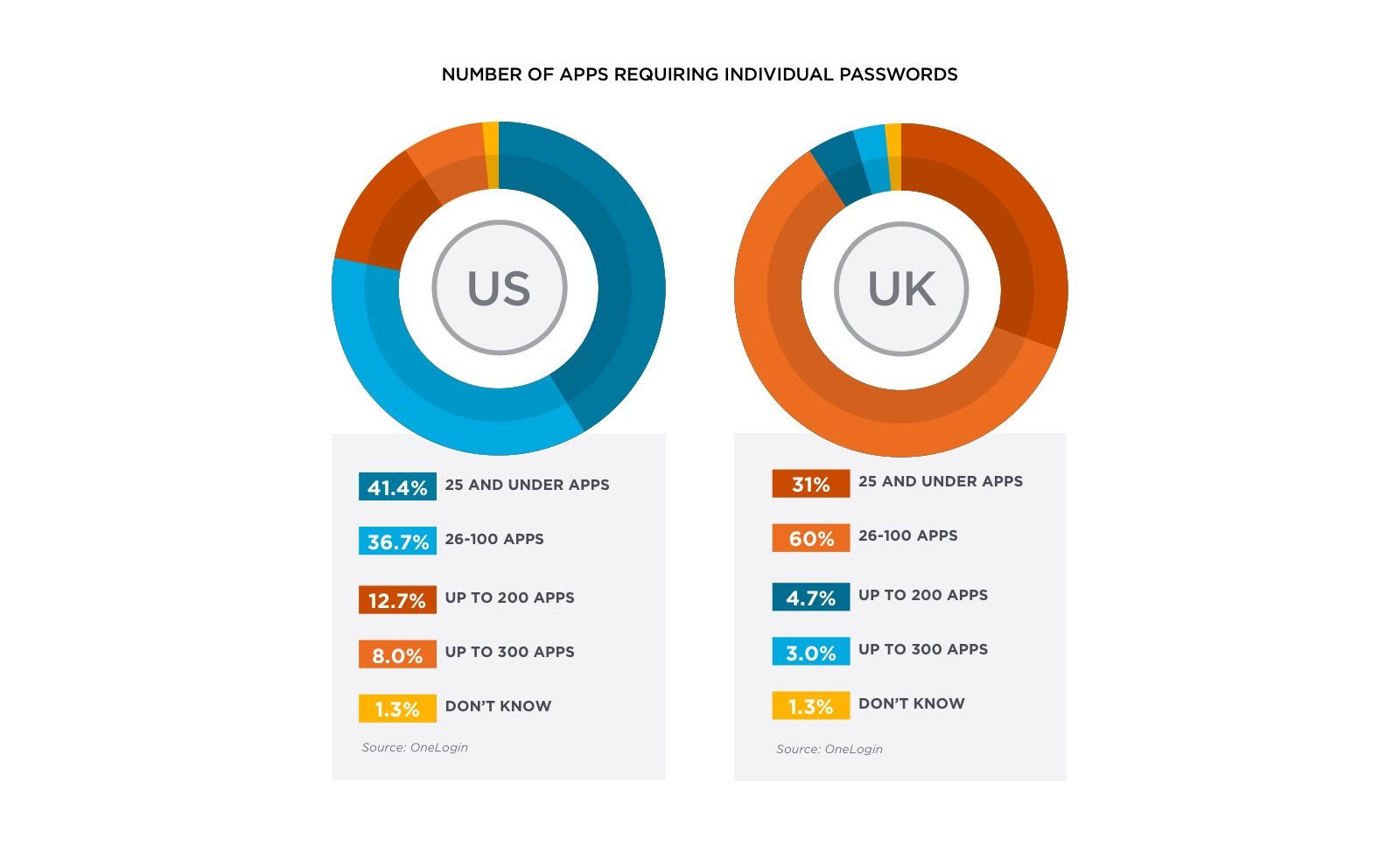
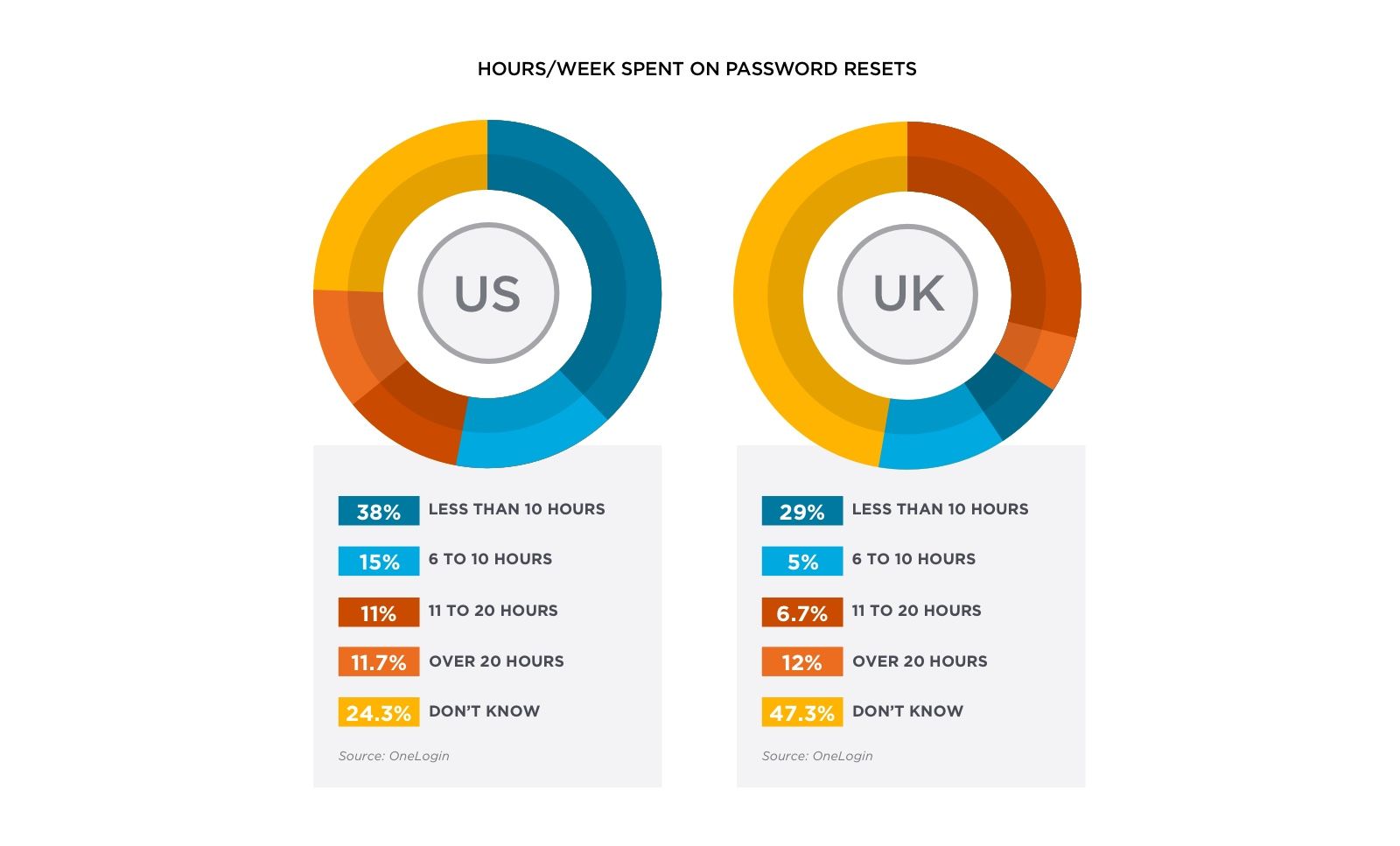
In the US, 36.7 percent of companies have 26 to 100 apps that require individual passwords. In the UK, a whopping 60 percent of companies have 26 to 100 apps that require individual passwords. That’s an awful lot of passwords and a huge burden on employees. The result: they’re forgetting their passwords. And calling on IT to reset them. In the US and the UK, IT spent an average of 2.5 months a year on password resets.
Sadly, 24.3 percent of US respondents and 47.3 percent of UK respondents didn’t even know how much time they were spending on password resets.
We all know that IT shouldn’t be the middle guy in password resets. But our survey found that most companies still aren’t enabling self-service password resets, eliminating passwords with single sign-on (SSO), nor securing access with multi-factor authentication (MFA). This despite the fact that such tools are exactly what the latest password guidelines call for.
The numbers are abysmal in the US, with only 42 percent of companies using SSO and 42 percent requiring MFA. In the UK, the numbers are a little better for SSO, with just over half (53 percent) of companies using SSO, but less than a third (29.7 percent) requiring MFA.
There’s more to discover in our survey, including information about provisioning, the breakdown of time spent on password resets, and details about the differences in how large and small companies deal with passwords. But the takeaway is simple: Businesses remain at risk of a data breach due to poor password hygiene.
To learn more about the role of passwords in the battle with hackers, see our white paper Winning the battle over passwords.

