What is a DDoS Attack?
A distributed denial-of-service (DDoS) attack occurs when a group of systems flood a server with fraudulent traffic. Eventually, the server is overwhelmed, causing it to either go down, or become unresponsive, even to legitimate requests.
From early 2020 to 2021, we have seen a 341% growth in the number of DDoS attacks. This is mainly because the pandemic forced many businesses to go digital, which naturally made them more susceptible to cyberattacks.
DDoS attacks are one of the most feared cyberattacks, and for good reason. A well-conducted DDoS attack can be virtually impossible to prevent and really difficult to stop. They can start at any time and cripple servers of even the most sophisticated IT companies. In 2018, GitHub was hit by the then-largest-ever DDoS attack, which flooded their servers with over 120 million data packets every second.
Regardless of the scale of attack, the underlying theme is always the same. Bombard a server with more requests than it can handle. Continue doing so until it either crashes or stops responding. Service disruptions can often take hours to remediate causing huge financial losses.
The Anatomy of a DDoS Attack
Instead of delving into technical details, let’s instead consider an analogy. Suppose that you run a takeaway burger joint. Customers place their orders by phone and pick them up when they are ready. One day, a prankster makes multiple calls to your place, ordering 100 burgers in total.
This is enough to keep all your cooks occupied, so you stop taking new orders. However, the prankster never picks up the burgers. Not only were all your resources wasted on entertaining fake orders, you were also not able to cater to real customers.
This can be annoying but easy to prevent since it’s just one person placing all the false orders. You can simply block their number, and the problem is solved. The same situation can happen on a server. One malicious client can send tons of fake requests to a server, hampering its ability to respond to real users.
But just like in our example, detecting one fake client is easy; the server can just block all incoming requests from it. This type of attack is known as a denial-of-service (DoS) attack, the precursor of modern DDoS attacks.
Now, let’s suppose there are multiple pranksters calling your burger joint. Your landline never stops ringing, and it’s virtually impossible to tell a real customer from a fake one. You can’t just block numbers either, as some of them may belong to actual customers. Your entire operation is paralyzed. This is exactly what happens when a server experiences a DDoS attack. Hackers make fake traffic coming in from multiple machines, look just like real, and a server/network/website inevitably breaks down.
Why do DDoS Attacks Happen?
Some of the main reasons for DDoS attacks are:
- Ransom: Attackers usually demand ransom after conducting DDoS attacks. However, at times, a ransom note threatening an attack can also be sent beforehand.
- Hacktivism: DDoS attacks are also used to voice opinion. Hacktivists can carry out a DDoS attack to show their support or opposition to a regulation, person, or company.
- Competition: A 2017 survey revealed that over 40% of companies that were hit by a DDoS attack blame their competition for it. This seems even more plausible considering that you can now buy a week-long DDoS attack for a mere $150.
Types of DDoS Attacks
Even though the end goal of a DDoS attack is always to overwhelm the system, the means to achieve the goal can differ. Three broad types of DDoS attacks are as follows.
1. Application layer attacks
The application layer is where the server generates the response to an incoming client request. For example, if a user enters http://www.xyz.com/learning/ on their browser, an HTTP request is sent to the server, requesting the learning page. The server will fetch all the information related to the page, package it in a response, and send it back to the browser.
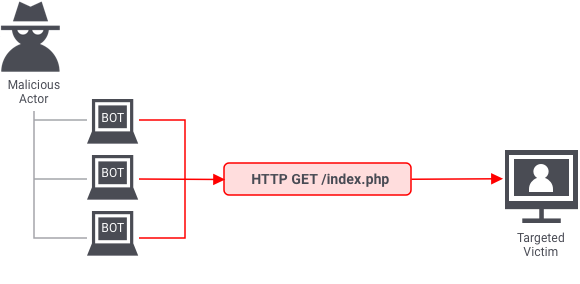
This information fetching and packaging happens on the application layer. An application layer attack occurs when a hacker uses different bots/machines to repeatedly request the same resource from the server, eventually overwhelming it.
The most common type of application layer attacks are the HTTP flood attacks in which malicious actors just keep sending various HTTP requests to a server using different IP addresses. One example of this is asking a server to generate PDF documents over and over again. Since the IP address and other identifiers change in every request, the server can’t detect that it’s being attacked.
2. Protocol attacks
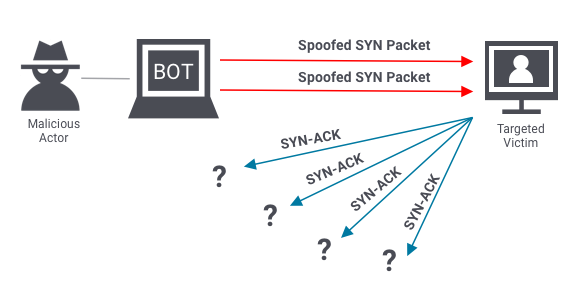
Protocol attacks look to exhaust resources of a server or those of its networking systems like firewalls, routing engines, or load-balancers. An example of a protocol attack is the SYN flood attack.
Before two computers can initiate a secure communication channel – they must perform a TCP handshake. A TCP handshake is a means for two parties to exchange preliminary information. A SYN packet is typically the first step of the TCP handshake, indicating to the server that the client wants to start a new channel.
In a SYN flood attack, the attacker floods the server with numerous SYN packets, each containing spoofed IP addresses. The server responds to each packet (via SYN-ACKs), requesting the client to complete the handshake. However, the client(s) never respond, and the server keeps waiting. Eventually, it crashes after waiting too long for too many responses.
3. Volumetric attacks
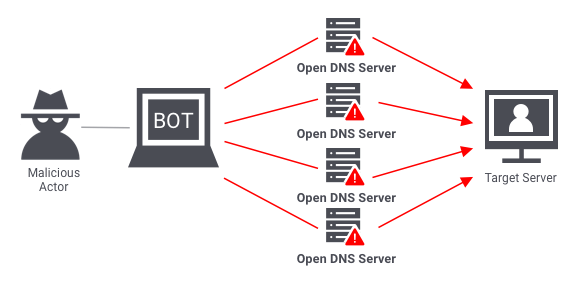
Volumetric attacks are conducted by bombarding a server with so much traffic that its bandwidth gets completely exhausted. The most common example of a volumetric attack is the DNS amplification attack.
In such an attack, a malicious actor sends requests to a DNS server, using the spoofed IP address of the target. The DNS server then sends its response to the target server. When done at scale, the delugeof DNS responses can wreak havoc on the target server.
Stopping an In-Progress DDoS Attack
To be able to stop a DDoS attack, you must know the most common symptoms.
Usual DDoS symptoms
- Large amounts of traffic coming from clients with same or similar characteristics. E.g. device type, browser type/version, IP or IP range, and location etc.
- An exponential, unexpected rise in traffic at a single endpoint/server.
- A server starts repeatedly crashing for no reason.
- Your website is taking too long to respond to requests.
Responding to a DDoS attack
Once you have identified a DDoS attack, it’s important to act quickly as it gives you an opportunity to prevent serious downtime. If you wait too long, your server may start crashing, and full recovery may take hours.
The hardest part about mitigating a DDoS attack is that often it’s virtually impossible to do so without impacting legitimate traffic. This is because attackers go to great lengths to masquerade fake traffic as real. With that said, here are some ways you can respond:
- Blackhole filtering: Go through incoming traffic and determine a limitation criterion. Use the criterion to route malicious traffic into a blackhole, essentially dropping it.
- Casting: Distribute the traffic across multiple servers, increasing your capacity, and decreasing the chances of individual servers getting overwhelmed.
- IP Blocking: If you are noticing unexpectedly high traffic from the same range of IP addresses, block them.
Is the breach notifiable?
According to GDPR, you must notify the Information Commissioner’s Office (ICO) if your breach poses a risk to the rights and freedoms of people. If you judge the risk to be unlikely, you aren’t liable to report it. However, if you decide not to report a breach, you should document your decision, as you could later be asked to justify it.
Preventing a DDoS Attack
Stopping an active DDoS attack can be hard and may affect your legitimate users. This is why it’s important to take a preemptive approach. In addition to the preventive measures mentioned below, you should also create an emergency DDoS incident response plan, as even the best defenses can sometimes succumb to sophisticated attacks.
- Real-time packet analysis: Analyze packets based on different rules, as they enter your system, discarding the potentially malicious ones.
- DDoS defense system (DDS): A DDS can detect legitimate-looking content with malicious intent. It protects against both protocol and volumetric attacks, without requiring any human intervention.
- Web application firewall: Web application firewalls (WAF) are a great tool to mitigate application layer DDoS attacks. They give you a way to filter incoming requests, based on different rules, which can also be added on-the-fly, in response to an attack.
- Rate limiting: Limit the number of requests a server can entertain over a certain time period.
